 Discussions regarding the importance of software security are nothing new. However, given the escalation in both the number and intensity of cyberattacks, and the fact that even decade-old vulnerabilities are still being exploited, the importance of security has never been greater.
Discussions regarding the importance of software security are nothing new. However, given the escalation in both the number and intensity of cyberattacks, and the fact that even decade-old vulnerabilities are still being exploited, the importance of security has never been greater.
For application developers, the stakes are especially high. According to research firm Gartner, nearly 80 percent of security breaches occur at the application layer. Furthermore, per Verizon’s 2016 Data Breach Investigation Report, increasingly common web applications are the most prevalent source of breaches —and data loss.
Vulnerabilities and the breaches they encourage are no longer merely headaches for developers, either. Software solution customers are increasingly demanding security in the products they use, often requiring evidence that code is undergoing appropriate security evaluation and testing—and requiring proof that the solutions they purchase are free of security defects.
Consequently, executive owners in the companies that create and sell these solutions are also more cognizant of not only security threats but the potential financial impact and legal ramifications they might have. As corporate responsibilities in the secure production of software solutions increase, business leaders are mandating that sound security practices be incorporated into the software development lifecycle (SDLC). In today’s market, developers who fail to follow appropriate security procedures or ignore the requisite to remediate issues do so at their peril.
To reduce the odds of having applications exploited, developing organizations must focus on security, not only at the end of the development cycle, and certainly not solely as a response to issues found in production. Rather, security must be built into the entire SDLC, beginning with a secure development process and continuing with robust security testing and swift action on identified vulnerabilities. Once applications are released to production, ongoing monitoring and further remediation are imperative to assure end-to-end security. With every code change or periodic release, the cycle begins again.
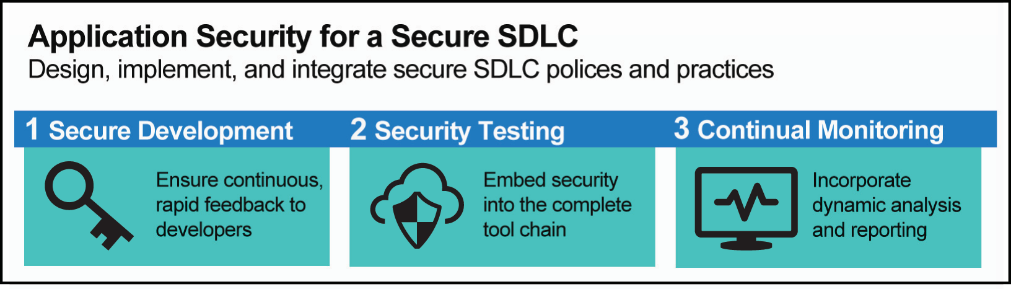
We recognize that for many firms this is easier said than done. Software teams unaccustomed to such an approach often feel forced to choose between seeking out and fixing security vulnerabilities in existing applications or finding time to incorporate security best practices into the SDLC for both existing applications and those under development.
The reality is that they need to do both. This conundrum is akin to a common technology challenge from a decade or so ago. Then, many companies got mired into a “break-fix” mode of IT management rather than focusing on improving practices holistically to mitigate the odds of more systems breaking.
This is precisely the problem many firms now face with application security. Teams focused on remediating vulnerabilities in existing applications keep their heads down, slinging code so fast that they cannot find time or energy to incorporate and follow best practices across the board.
We’ll say it right now: This practice needs to stop.
Of course, identifying and remediating vulnerabilities is important—even, vital—to application and corporate security. At the same time, however, organizations and their teams must also develop application security systems and programs that will bring them out of “post-release fix mode” and into a proactive future.
Fortunately, this is not new ground. Many progressive organizations have already accomplished this goal, and consulting firms such as ours work with customers on these efforts every day.
Security Tools to the Rescue
Additionally, software teams no longer need to shoulder security burdens on their own. Solutions now exist that facilitate application security by automating some of the most important tasks, which are often difficult and time-consuming to accomplish manually. One example we frequently recommend—and help organizations deploy effectively—is HPE Fortify, a vulnerability scanning platform that offers two different scanning models: static and dynamic.
Static and dynamic scanning are not opposites, with one scrutinizing existing applications and the other examining code under development. Rather, they are complementary.
Static code analysis is purpose-designed to identify security vulnerabilities efficiently in source code. Such analysis can—and should—be done early in the development lifecycle as well as throughout the life of the application, with code updates and other changes. Static code analysis offers the benefit of providing immediate feedback to developers on issues that might create vulnerabilities as they are introduced into code during any and all development activities.
Dynamic analysis, conversely, is performed on applications in a runtime environment. Used primarily for pre-release testing and for post-release monitoring, dynamic analyzers explore the attack surface of running applications to identify new types of vulnerabilities that are difficult to detect solely through source code analysis.
To illustrate how these solutions should work, we will use the tools in HPE Fortify as an example.
HPE Fortify Static Code Analyzer (SCA)
HPE Fortify SCA is a command-line-based static code analyzer that can integrate into any environment through scripts, plugins, and GUI tools. It is designed to run in mixed development and production environments. As such, it supports a wide variety of languages, platforms, and frameworks and supports all major platforms, build environments, and integrated development environments.
HPE Fortify SCA prioritizes the vulnerabilities it discovers, delivering them categorized and ranked by risk to provide developers with a functional action plan. HPE’s Fortify security experts continually expand and update the security coding rules used the HPE Fortify SCA, making it the most complete set of rules available in any static code analysis tool.
HPE WebInspect (Dynamic Analysis)
HPE WebInspect is designed not only to find vulnerabilities in existing applications but also to identify them in application updates and other releases. This type of analysis can be invaluable, since release cycles are often time constrained, encouraging teams to bypass security checks.
The WebInspect agent crawls each application, searching for new types of vulnerabilities that are more readily detectable in a runtime environment. Through the use of sophisticated algorithms, it can also detect web services and capture URL rewrites (a rule-based rewriting mechanism for modifying request URLs before they are processed by a web server). Depending on the variant of HPE WebInspect, organizations can also implement recurrent scanning, with results sent to a centralized vulnerability management interface.
Of course, code and application analysis tools are only part of a comprehensive application security program, which should also include true integration of security into the SDLC, including security testing and QA with every code change. Furthermore, teams must be appropriately trained, not only in the elements of the security plan but also in the practical application of its approaches.
In future blogs, we will provide more insight into how organizations can achieve meaningful application security across the SDLC. To request more information, now, contact Saltworks LLC at 678.819.5300.